Cleven
(→System Configuration Dialog) |
(note for not up to date information.) |
||
| Line 1: | Line 1: | ||
| + | ''NOTE: This page is currently updated to reflect the latest stable version. Some information here might be out of date. --[[User:saturn|saturn]] 13:39, 11 February 2012 (UTC)'' | ||
| + | |||
The Cleven application is a user interface to the aircrack-ng for the [[Nokia N900|N900]] device. | The Cleven application is a user interface to the aircrack-ng for the [[Nokia N900|N900]] device. | ||
Revision as of 13:40, 11 February 2012
NOTE: This page is currently updated to reflect the latest stable version. Some information here might be out of date. --saturn 13:39, 11 February 2012 (UTC)
The Cleven application is a user interface to the aircrack-ng for the N900 device.
It provides the ability to easily configure the injection drivers, scan for surrounding stations, and, using injection and authentication or deauthentication, capture Identification Vector keys.
In addition, it provides interfaces to decrypt the captured files and manage the successful attacks.
It has been created with PyQT (PyQt v4.7.5 for Python v2.6) and the functionality is provided by Python.
Contents |
Installation
The application can be installed directly by the Application Manager (HAM) from the Extras repositories (check here for its status).
Dependencies
Included
The application depends on:
- python2.5
- python2.5-qt4-gui
- python2.5-qt4-core
- python2.5-qt4-maemo5
- aircrack-ng
- macchanger
- libpcap0.8
Expected
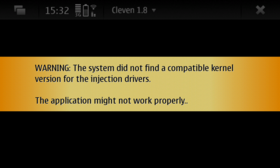
In order to load the bleeding edge drivers it expects a kernel that can support it. The application on startup checks and reports possible inability of correct function if one of the following power kernels are not used:
- 46-wl1
- 47
- 48 (unconfirmed; same issues with the drivers have been reported)
- 49
Suggested
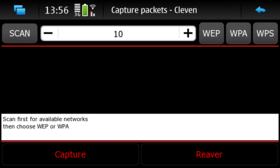
The application optionally supports the Reaver and Walsh implementations of the WPS attack.
Quote: Reaver implements a brute force attack against Wifi Protected Setup (WPS) registrar PINs in order to recover WPA/WPA2 passphrases, as described in viehboeck_wps.pdf.
The following binaries need to be available for relevant options to become visible:
- reaver
- walsh
(atm the support is for versions 1.4 as of reaver-wps; read also the release changelog for additional info).
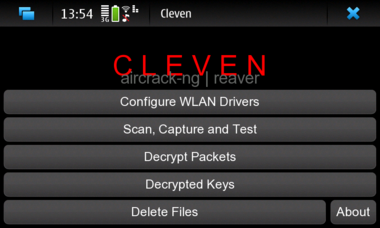
Key features
- Includes the injection drivers (courtesy of lxp; see here for more info and if you like it consider donating to him.).
- Original MAC is stored and restored on drivers load/unload.
- Handles correctly spaces and special characters in the Network names
- The Network names are sorted by name (note: hidden APs are not supported/shown).
- Decryption can be done for data captured over multiple sessions.
- Successful decrypted keys are stored in a separate folder.
- Supports Reaver and Walsh WPS attacks.
Usage
Startup Dialog
Starting the application shows a splash screen.
In the background, a check is been made if the kernel available supports the injection drivers. In the error case, a warning message is displayed for the incompatibility.
After all checks and the loading completes the main window appears that provides all available options.
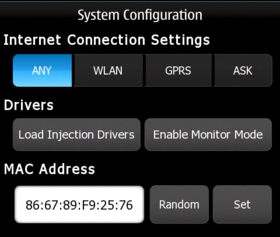
Drivers Configuration Dialog
As soon as the application starts the System Configuration dialog is shown.
It is recommended to set the Internet Connection Setting to ASK so that the system does not try to connect while the system tries to use the monitor mode.
The next steps will be to load the injection drivers and enable the monitor mode.
The MAC address can be also changed to a random one or in the case of MAC filtering by the Access Point to an already connected by typing the value and pressing SET.
Note 1: The same configuration dialog can be accessed at the end of the session (i.e. from the Drop down menu) to revert the settings.
Note 2: The default system MAC address will be restored automatically when the drivers get unloaded.
Scan Window
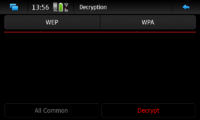
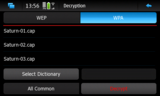
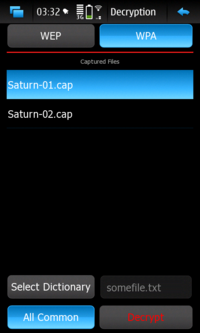
Decryption Window
The "Decryption Window" sorts files alphabetically and by security type.
Using the "All Common" button it instructs the decryption to consider all files captured from the same network on different sessions.
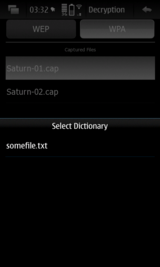
When the WPA security type is chosen then also a button for selecting a dictionary appears.
Pressing this button a dialog appears that shows the dictionaries stored in/home/user/.cleven/dictionariesand allows the selection of the dictionary to be used for the decryption.
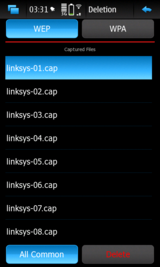
Deletion of files
From the Decryption window, pressing the menubar will provide the option to enable the "Deletion Mode". While in this mode, pressing the menubar again will give the opposite option, i.e. exit from the mode.
The "Deletion Mode" keeps the same appearance as the parent window and sorts files alphabetically and by security type.
Using the "All Common" button it is possible to delete all files captured from the same network.
Keys Management Window
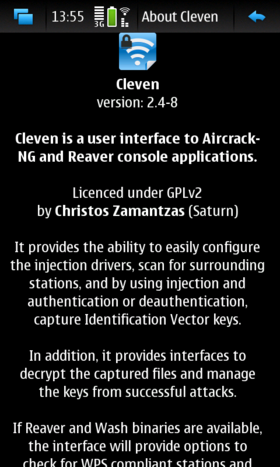
About
In the about window one can find the version of the application running as well as buttons to connect to additional documentation (like all the rest of the windows it supports rotation).
Versions
2.4-8 (Development)
CHANGE: Support for the latest wash (> r100) output file readout. NEW: Added reaver option "--dh-small"; seems to help not overloading/crashing some AP too fast. CHANGE: Removed reaver option "--essid"; avoid problem with special characters in the name. CHANGE: Replaced reaver option "-vv" with the less verbose "-v". CHANGE: Redone keys window; new logic: - Added "Delete" and "Copy" buttons, i.e. file remove and copy to clipboard. - Removed "Read Keys" button; action is triggered automatically. NEW: Removed menu items; the About is accessible from the main window through a new button. CHANGE: Modification of labels in the main window. CHANGE: Modification of the About window text; added few words on reaver. NEW: Added option and rules for the deletion of the "replay_arp" leftover files.
** INSTRUCTIONS for new features: Add reaver, reaven.db and wash binaries in /home/user/.reaver/ and re-start Cleven for the links to be created. This version of Cleven was designed to work with versions up to release r100 of reaver and wash.
2.4-7
FIX: Dialog with keys was closing too fast. CHANGE: Removed channel option from the reaver call.
** INSTRUCTIONS for new features: Add reaver, reaven.db and wash binaries in /home/user/.reaver/ and re-start Cleven for the links to be created. This version of Cleven was designed to work with versions up to release r90 of reaver and wash.
2.4-6
FIX: Authentication command mismatch between the UI and script. FIX: Capture could fail in some cases if initiated from the WPS selection. NEW: Added detection on AP names for the single and double quote characters as well as a few more symbols like brackets etc.
** INSTRUCTIONS for new features: Add reaver, reaven.db and wash binaries in /home/user/.reaver/ and re-start Cleven for the links to be created. This version of Cleven was designed to work with versions up to release r90 of reaver and wash.
2.4-5
CHANGE: Added logging for the Authentication and Capture command in /tmp/cleven.log CHANGE: Removed the -essid option from the authentication (credits: StefanL, g0r) CHANGE: Update for latest (r90) of reaven and wash; walsh has been deprecated. NEW: Added reaven.db support
2.4-3
FIX: Further correction in the creation of the symbolic links for reaver and walsh. FIX: walsh output file would persist; now it is removed explicitly after each scan. CHANGE: Added build number in main and about windows. ** INSTRUCTIONS for new features: Add reaver and walsh binaries in /home/user/.reaver/ and re-start Cleven for the links to be created. This version of Cleven was designed to work with up to version 1.3 of reaver and walsh.
2.4-2
FIX: Correction for missing symbolic links creation for reaver and walsh.
** INSTRUCTIONS for new features: Add reaver and walsh binaries in /home/user/.reaver/ and re-start Cleven for the links to be created.
2.4-1
** Merge with EXPERIMENTAL version of Cleven. CHANGE: Removed wpscrack.py and related dependencies. CHANGE: Removed connect_reaver.sh; not needed any more. NEW: If during installation, upgrade or start up of the application it finds reaver and/or walsh in the folder /home/user/.reaver then it makes copies and links them with the program. CHANGE: Added in the call for reaver option "-a"; it will restore previous session automatically. CHANGE: Modification of the Capture UI. NEW: Addition of a WPS button; the option will become available if walsh is operational, otherwise the option will be hidden. NEW: If walsh is available it will be used to sort WPS compliant APs only; NEW: If reaver is available and operational the option to test AP with will become visible.
** INSTRUCTIONS for new features: Add reaver and walsh binaries in /home/user/.reaver/ and re-start Cleven for the links to be created.
2.2-1
NEW: Information on the power of an AP. CHANGE: Modification in the main window (minor). CHANGE: Update and cleanup of the debian install scripts.
2.1-4
* Added preinstall script to clean up old files. * Fix in the start-up window. * Modification in the main window to give better names to the buttons. * Update in the disclaimer.
...some version logs missing...
2.1-1
* New Main window to provide faster and easier access to features. * Modifications of classes to be called from the main window. * Deprecation of "Delete captured files" menu option. * Fix in the WPA deauthentication. * Refactoring and code cleanup in multiple places.
Issues
* WPA deauthentication does not collect client's MAC.
1.12-6
* Fix several regression issues introduced in version 1.12-5 due to mishandling of move and merge commands in SVN.
1.12-5
* Fix in the filename manipulations (avoid errors when AP names include "-" characters). [patch from mikemorrison] * improved the startup screen. * fix in the About window. * addition of kernel-power v49 as a valid configuration.
1.11-2
* Fix (proper) for WAP authentication to accept spaces in network names. * Addition to store only IVs when in WEP capture (and save space).
1.10-1 (stable)
* Workarournd for WAP authentication to accept spaces in network names.
Issues
* WPA deauthentication does not collect client's MAC.
1.9-1
* Fixed check for the compatible kernel versions. * Redesign of the decryption window. Added new dialog and button for selecting the dictionary for the WPA decryption.
Issues
* WAP authentication do not accept spaces in network names. * WPA deauthentication does not collect client's MAC.
1.8-2
* Fixed check for the compatible kernel versions.
1.8-1
* Added skip button for the intro page. * Added check for compatible kernel version.
1.7-1
First public release...
Key dependencies and features: * The package depends on aircrack-ng, macchanger and expects power kernel >= 46. * Includes the injection drivers (courtesy of lxp) * Original MAC is stored and restored on exit. * Handles correctly spaces and special characters in the ESSID names * The ESSID names are sorted and the hidden are not shown. * Decryption can be done for data captured over multiple sessions. * Successful decrypted keys are stored in a seperate folder. * Management of captured files.
License
This program is free software; you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation; version 2 only.
Disclaimer
This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details.
Also, the application provided is to be used for educational purposes only. The application creator is in no way responsible for any misuse of the information provided. All of the information in this application is meant to help develop a hacker defence attitude in order to prevent the attacks discussed. In no way should you use the information to cause any kind of damage directly or indirectly. The word "Hack" or "Hacking" should be regarded as "Ethical Hack" or "Ethical Hacking" respectively. You implement the information given at your own risk.