Enterprise - Tried and tested provisioning strategies
(→Components) |
(wikify slightly) |
||
| (5 intermediate revisions not shown) | |||
| Line 3: | Line 3: | ||
In the pictures, thick red dashed lines represent ''logical'' connections between actors. If a line has an arrow, it represents direction of the initiation of the communication (which is the direction of the required firewall rule). | In the pictures, thick red dashed lines represent ''logical'' connections between actors. If a line has an arrow, it represents direction of the initiation of the communication (which is the direction of the required firewall rule). | ||
| - | = Strategy 1: Simple and direct = | + | == Strategy 1: Simple and direct == |
This is the most simple strategy and the most straightforward to implement. In this strategy, direct enrollment is used. Also, since the whole process takes place at the same server, the line between the enrollment and the bootstrapping phases are blurred. | This is the most simple strategy and the most straightforward to implement. In this strategy, direct enrollment is used. Also, since the whole process takes place at the same server, the line between the enrollment and the bootstrapping phases are blurred. | ||
| - | [[Image:Combined_Enrollment_Installation_server_at_lobby_network.png | + | [[Image:Combined_Enrollment_Installation_server_at_lobby_network.png|thumb|900px|alt=Diagram of a combined ecrollment/installation server installed at a lobby network|Figure 1: Combined Enrollment/Installation server at lobby network]] |
| - | + | ||
| + | === The process === | ||
| - | |||
# Since repositories at the public Internet are usually not accessible, to avoid Application Manager halting problem, the user needs to disable all repositories on the device. Alternatively, the user may authenticate him/herself to pass through the Access Gateway. | # Since repositories at the public Internet are usually not accessible, to avoid Application Manager halting problem, the user needs to disable all repositories on the device. Alternatively, the user may authenticate him/herself to pass through the Access Gateway. | ||
# The user connects directly, using the device keyboard and display, to a URL on the Enrollment/Installation server. | # The user connects directly, using the device keyboard and display, to a URL on the Enrollment/Installation server. | ||
| Line 16: | Line 16: | ||
# The Enrollment/Installation server generates the <span style="color:#0000ff" title="Enterprise User Configuration File: A container for user-specific and enterprise-specific configuration values collected from various sources. ">EUF</span> and bootstraps the installation. | # The Enrollment/Installation server generates the <span style="color:#0000ff" title="Enterprise User Configuration File: A container for user-specific and enterprise-specific configuration values collected from various sources. ">EUF</span> and bootstraps the installation. | ||
| - | == Components == | + | === Components === |
* Web application (CGI script) running at the Enrollment/Installation server. An example (skeleton) CGI script will be provided soon in gagare.maemo.org that corresponds to the examples given for the [[Enterprise_Device_Configuration|device side configuration]]. | * Web application (CGI script) running at the Enrollment/Installation server. An example (skeleton) CGI script will be provided soon in gagare.maemo.org that corresponds to the examples given for the [[Enterprise_Device_Configuration|device side configuration]]. | ||
| - | == Firewall rules == | + | === Firewall rules === |
| - | {| | + | {| class="wikitable" |
| + | |+ Firewall rules: Simple and direct strategy | ||
| + | |- | ||
! Source !! Target !! Protocol !! Direction !! Notes | ! Source !! Target !! Protocol !! Direction !! Notes | ||
|- | |- | ||
| Line 30: | Line 32: | ||
|- | |- | ||
| Admin server || Installation server || HTTPS (443)||Outbound || Optional | | Admin server || Installation server || HTTPS (443)||Outbound || Optional | ||
| - | |||
|} | |} | ||
| - | == Security considerations == | + | === Security considerations === |
* The Enterprise User Database must be accessible. This needs a hole on its inbound firewall. This is a concern in case the Enrollment Server is compromized. | * The Enterprise User Database must be accessible. This needs a hole on its inbound firewall. This is a concern in case the Enrollment Server is compromized. | ||
* The user password travels (in encrypted form) in an insecure network outside the corporate firewalls. | * The user password travels (in encrypted form) in an insecure network outside the corporate firewalls. | ||
| - | == Pros and cons == | + | === Pros and cons === |
* + Simple and straightforward to implement. | * + Simple and straightforward to implement. | ||
* - Potentially tedious to the user, at worst case they have to authenticate themselves '''twice''' using the device keyboad (first for Access Gateway, then for Enrollment Server). | * - Potentially tedious to the user, at worst case they have to authenticate themselves '''twice''' using the device keyboad (first for Access Gateway, then for Enrollment Server). | ||
| - | = Strategy 2: SMS based = | + | == Strategy 2: SMS based == |
| - | Although the device does not currently support OTA configuration messages, there is a way to utilize SMS messages in provisioning. | + | Although the device does not currently support OTA configuration messages, there is a way to utilize SMS messages in provisioning. The idea is to deliver the configuration data from Enrollment Server to Installation Server behind the scenes, and simultaneously deliver to the device via SMS a one-time time-limited URL which enables access to the configuration data. |
| - | The idea is to deliver the configuration data from Enrollment Server to Installation Server behind the scenes, and simultaneously deliver to the device via SMS a one-time time-limited URL which enables access to the configuration data. | + | |
This strategy is more complicated to implement but easier to use. It uses indirect enrollment. | This strategy is more complicated to implement but easier to use. It uses indirect enrollment. | ||
| - | [[Image:Separate_Enrollment_and_Installation_servers.png | + | [[Image:Separate_Enrollment_and_Installation_servers.png|thumb|900px|alt=Diagram of separate enrollment and installation servers|Figure 2: Separate Enrollment and Installation servers]] |
| - | + | ||
| - | == The process == | + | === The process === |
# Since repositories at the public Internet are usually not accessible, to avoid Application Manager halting problem, the user needs to disable all repositories from the device. Alternatively, the user may authenticate him/herself to pass through the Access Gateway. | # Since repositories at the public Internet are usually not accessible, to avoid Application Manager halting problem, the user needs to disable all repositories from the device. Alternatively, the user may authenticate him/herself to pass through the Access Gateway. | ||
| Line 60: | Line 59: | ||
# Enrollment Server generates a random pin code. | # Enrollment Server generates a random pin code. | ||
# Enrollment Server generates the <span style="color:#0000ff" title="Enterprise User Configuration File: A container for user-specific and enterprise-specific configuration values collected from various sources. ">EUF</span> and transfers it, along with the pin code, to Installation Server. | # Enrollment Server generates the <span style="color:#0000ff" title="Enterprise User Configuration File: A container for user-specific and enterprise-specific configuration values collected from various sources. ">EUF</span> and transfers it, along with the pin code, to Installation Server. | ||
| - | # Enrollment Server generates a URL which points to a CGI script at the Installation Server and contains the pin code. For example, <code>https://server.example.com/indirect.cgi?pincode=aa913a5b-6558-44a5-a501-bbf5c81078d3</code>. | + | # Enrollment Server generates a URL which points to a CGI script at the Installation Server and contains the pin code. For example, <code><nowiki>https://server.example.com/indirect.cgi?pincode=aa913a5b-6558-44a5-a501-bbf5c81078d3</nowiki></code>. |
# Enrollment Server generates an SMS message which contains the URL and sends it to the device using SMS gateway. | # Enrollment Server generates an SMS message which contains the URL and sends it to the device using SMS gateway. | ||
# When the user opens the SMS message at the device, Conversations application displays the URL as a clickable link. When the user clicks the link, the Web Browser application is invoked and the URL is opened. | # When the user opens the SMS message at the device, Conversations application displays the URL as a clickable link. When the user clicks the link, the Web Browser application is invoked and the URL is opened. | ||
| Line 70: | Line 69: | ||
To clean up, Installation server runs a cron job at every few minutes, removing all generated temporary files which are older than predefined time limit | To clean up, Installation server runs a cron job at every few minutes, removing all generated temporary files which are older than predefined time limit | ||
| - | == Components == | + | === Components === |
* Web application (CGI script) running at Enrollment Server | * Web application (CGI script) running at Enrollment Server | ||
| Line 76: | Line 75: | ||
* SMS gateway | * SMS gateway | ||
| - | == Firewall rules == | + | === Firewall rules === |
| - | {| | + | {| class="wikitable" |
| + | |+ Firewall rules: SMS-based strategy | ||
|- | |- | ||
| - | + | ! Source !! Target !! Protocol !! Direction !! Notes | |
|- | |- | ||
|Admin server || Installation server || SSH (22)||Outbound || | |Admin server || Installation server || SSH (22)||Outbound || | ||
| Line 87: | Line 87: | ||
|- | |- | ||
|Admin server || Installation server || HTTPS (443)||Outbound ||Optional | |Admin server || Installation server || HTTPS (443)||Outbound ||Optional | ||
| - | |||
| - | |||
|} | |} | ||
| - | == Security considerations == | + | === Security considerations === |
| - | * | + | * PIN code can and should be fairly long, longer than a typical username and password together. |
* No need for inbound firewall holes. | * No need for inbound firewall holes. | ||
* User password does not travel outside corporate intranet. | * User password does not travel outside corporate intranet. | ||
| - | == Pros and cons == | + | === Pros and cons === |
* + The obvious advantage of indirect enrollment combined with SMS-URL based bootstrapping is the minimization of user interaction performed from the device keyboard and display. Writing the provisioning URL, username and password from the device keyboard are all avoided. Most of the user interaction can be performed using full size keyboard and display, only couple of touchscreen clicks is left to be to done at the device. | * + The obvious advantage of indirect enrollment combined with SMS-URL based bootstrapping is the minimization of user interaction performed from the device keyboard and display. Writing the provisioning URL, username and password from the device keyboard are all avoided. Most of the user interaction can be performed using full size keyboard and display, only couple of touchscreen clicks is left to be to done at the device. | ||
| Line 103: | Line 101: | ||
* - Requires more servers (not necessarily if Admin server can host as Enrollment server as well) | * - Requires more servers (not necessarily if Admin server can host as Enrollment server as well) | ||
| - | = Strategy 3: Offline installation = | + | == Strategy 3: Offline installation == |
This strategy is probably used as a complement to previous strategies. The server topology may be similar to either of the descried ones. | This strategy is probably used as a complement to previous strategies. The server topology may be similar to either of the descried ones. | ||
| Line 109: | Line 107: | ||
The most important use case for this strategy is to enable provisioning for users located at remote sites and unable to access corporate WLAN. | The most important use case for this strategy is to enable provisioning for users located at remote sites and unable to access corporate WLAN. | ||
| - | == The process == | + | === The process === |
# To avoid Application Manager halting problem, user needs to disable all repositories from the device. Or alternatively, connect to a 3G network. | # To avoid Application Manager halting problem, user needs to disable all repositories from the device. Or alternatively, connect to a 3G network. | ||
| Line 116: | Line 114: | ||
# Enrollment Server generates a random pin code. | # Enrollment Server generates a random pin code. | ||
# Enrollment Server generates <span style="color:#0000ff" title="Enterprise User Configuration File: A container for user-specific and enterprise-specific configuration values collected from various sources. ">EUF</span>, transfers it and the pin code to Installation server. | # Enrollment Server generates <span style="color:#0000ff" title="Enterprise User Configuration File: A container for user-specific and enterprise-specific configuration values collected from various sources. ">EUF</span>, transfers it and the pin code to Installation server. | ||
| - | # Enrollment Server generates an URL which points to a CGI script at the Installation Server and contains the pin code. For example, <code>https://server.example.com/offline.cgi?pincode=a913a5bXTgd</code>. | + | # Enrollment Server generates an URL which points to a CGI script at the Installation Server and contains the pin code. For example, <code><nowiki>https://server.example.com/offline.cgi?pincode=a913a5bXTgd</nowiki></code>. |
# Enrollment Server redirects the web browser to that URL, or presents a clickable link. | # Enrollment Server redirects the web browser to that URL, or presents a clickable link. | ||
# When the CGI script at the Installation Server is called, it checks if there is an <span style="color:#0000ff" title="Enterprise User Configuration File: A container for user-specific and enterprise-specific configuration values collected from various sources. ">EUF</span> matching the pincode. If yes, the script checks the age of the <span style="color:#0000ff" title="Enterprise User Configuration File: A container for user-specific and enterprise-specific configuration values collected from various sources. ">EUF</span>. If the file is older than a predefined time limit (e.g., 5 minutes), an error message is generated and processing stops. | # When the CGI script at the Installation Server is called, it checks if there is an <span style="color:#0000ff" title="Enterprise User Configuration File: A container for user-specific and enterprise-specific configuration values collected from various sources. ">EUF</span> matching the pincode. If yes, the script checks the age of the <span style="color:#0000ff" title="Enterprise User Configuration File: A container for user-specific and enterprise-specific configuration values collected from various sources. ">EUF</span>. If the file is older than a predefined time limit (e.g., 5 minutes), an error message is generated and processing stops. | ||
| Line 133: | Line 131: | ||
# User taps the install file to invoke the Application Manager, which installs the User Info package and all the packages in the dependency chain. | # User taps the install file to invoke the Application Manager, which installs the User Info package and all the packages in the dependency chain. | ||
| - | == Components == | + | === Components === |
* Web application (CGI script) running at Enrollment server | * Web application (CGI script) running at Enrollment server | ||
* Web application (CGI script) running at Installation server | * Web application (CGI script) running at Installation server | ||
| - | == Firewall rules == | + | === Firewall rules === |
Same as in previous two strategies, depending on which server topology is used | Same as in previous two strategies, depending on which server topology is used | ||
| - | == Security considerations == | + | === Security considerations === |
* None | * None | ||
| - | == Pros and cons == | + | === Pros and cons === |
* + Enables provisioning at remote locations | * + Enables provisioning at remote locations | ||
| Line 153: | Line 151: | ||
* - Presumably slow and storage space consuming | * - Presumably slow and storage space consuming | ||
| - | = Summary = | + | == Summary == |
| + | |||
| + | Here we looked at the tried out solutions for provisioning but some readers might be interested to read our [[Enterprise Provisioning - Strategy Variations|alternative solution considerations]] or about [[Enterprise Provisioning - Future_Prospects|future prospects for provisioning]]. If on the other hand these solutions suited already your needs you can move onward to [[Enterprise Provisioning Summary|provisioning summary]]. | ||
| - | + | [[Category:Enterprise]] | |
Latest revision as of 11:18, 21 January 2011
Each of the provisioning strategies in this chapter are either in daily use or at least built and tested as proof-of concept.
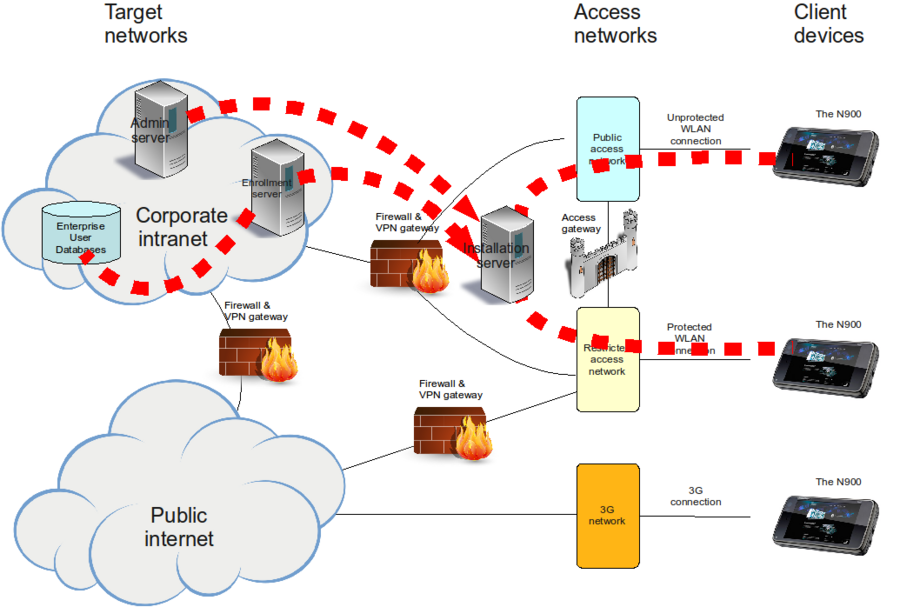
In the pictures, thick red dashed lines represent logical connections between actors. If a line has an arrow, it represents direction of the initiation of the communication (which is the direction of the required firewall rule).
Contents |
[edit] Strategy 1: Simple and direct
This is the most simple strategy and the most straightforward to implement. In this strategy, direct enrollment is used. Also, since the whole process takes place at the same server, the line between the enrollment and the bootstrapping phases are blurred.
[edit] The process
- Since repositories at the public Internet are usually not accessible, to avoid Application Manager halting problem, the user needs to disable all repositories on the device. Alternatively, the user may authenticate him/herself to pass through the Access Gateway.
- The user connects directly, using the device keyboard and display, to a URL on the Enrollment/Installation server.
- The user provides his/her credentials.
- The Enrollment/Installation server generates the EUF and bootstraps the installation.
[edit] Components
- Web application (CGI script) running at the Enrollment/Installation server. An example (skeleton) CGI script will be provided soon in gagare.maemo.org that corresponds to the examples given for the device side configuration.
[edit] Firewall rules
| Source | Target | Protocol | Direction | Notes |
|---|---|---|---|---|
| Enrollment server | Enterprise User Database | LDAPS (636) | Inbound | |
| Admin server | Installation server | SSH (22) | Outbound | |
| Admin server | Installation server | HTTPS (443) | Outbound | Optional |
[edit] Security considerations
- The Enterprise User Database must be accessible. This needs a hole on its inbound firewall. This is a concern in case the Enrollment Server is compromized.
- The user password travels (in encrypted form) in an insecure network outside the corporate firewalls.
[edit] Pros and cons
- + Simple and straightforward to implement.
- - Potentially tedious to the user, at worst case they have to authenticate themselves twice using the device keyboad (first for Access Gateway, then for Enrollment Server).
[edit] Strategy 2: SMS based
Although the device does not currently support OTA configuration messages, there is a way to utilize SMS messages in provisioning. The idea is to deliver the configuration data from Enrollment Server to Installation Server behind the scenes, and simultaneously deliver to the device via SMS a one-time time-limited URL which enables access to the configuration data.
This strategy is more complicated to implement but easier to use. It uses indirect enrollment.
[edit] The process
- Since repositories at the public Internet are usually not accessible, to avoid Application Manager halting problem, the user needs to disable all repositories from the device. Alternatively, the user may authenticate him/herself to pass through the Access Gateway.
- User connects to the Enrollment Server using a desktop computer and provides his/her credentials.
- Using the credentials, the Enrollment Server queries user information from Enterprise User Database, including the phone number of the users device.
- Enrollment Server generates a random pin code.
- Enrollment Server generates the EUF and transfers it, along with the pin code, to Installation Server.
- Enrollment Server generates a URL which points to a CGI script at the Installation Server and contains the pin code. For example,
https://server.example.com/indirect.cgi?pincode=aa913a5b-6558-44a5-a501-bbf5c81078d3. - Enrollment Server generates an SMS message which contains the URL and sends it to the device using SMS gateway.
- When the user opens the SMS message at the device, Conversations application displays the URL as a clickable link. When the user clicks the link, the Web Browser application is invoked and the URL is opened.
- When the CGI script at the Installation Server is called, it checks whether there is an EUF matching the pincode. If there is, the script checks the age of the EUF. If the file is older than a predefined time limit (e.g., 5 minutes) an error message is generated and processing stops.
- If the file age is OK, the script bootstraps the installation according selected bootstrapping strategy. "Via package" bootstrap strategy is probably more feasible, especially if ease of use is among the reasons.
- At the device, the Web Browser invokes the Application Manager, which installs the on-the-fly generated package and all packages in the dependency chain
- Post-install script runs and re-enables repositories disabled at step 1
To clean up, Installation server runs a cron job at every few minutes, removing all generated temporary files which are older than predefined time limit
[edit] Components
- Web application (CGI script) running at Enrollment Server
- Web application (CGI script) running at Installation Server
- SMS gateway
[edit] Firewall rules
| Source | Target | Protocol | Direction | Notes |
|---|---|---|---|---|
| Admin server | Installation server | SSH (22) | Outbound | |
| Enrollment server | Installation server | SSH (22) | Outbound | |
| Admin server | Installation server | HTTPS (443) | Outbound | Optional |
[edit] Security considerations
- PIN code can and should be fairly long, longer than a typical username and password together.
- No need for inbound firewall holes.
- User password does not travel outside corporate intranet.
[edit] Pros and cons
- + The obvious advantage of indirect enrollment combined with SMS-URL based bootstrapping is the minimization of user interaction performed from the device keyboard and display. Writing the provisioning URL, username and password from the device keyboard are all avoided. Most of the user interaction can be performed using full size keyboard and display, only couple of touchscreen clicks is left to be to done at the device.
- - A bit more laborious to implement
- - Requires more servers (not necessarily if Admin server can host as Enrollment server as well)
[edit] Strategy 3: Offline installation
This strategy is probably used as a complement to previous strategies. The server topology may be similar to either of the descried ones.
The most important use case for this strategy is to enable provisioning for users located at remote sites and unable to access corporate WLAN.
[edit] The process
- To avoid Application Manager halting problem, user needs to disable all repositories from the device. Or alternatively, connect to a 3G network.
- User connects to the Enrollment Server via a VPN connection to the corporate intranet using a desktop computer and provides his/her credentials.
- Using the credentials, the Enrollment Server queries the user information from the Enterprise User Database.
- Enrollment Server generates a random pin code.
- Enrollment Server generates EUF, transfers it and the pin code to Installation server.
- Enrollment Server generates an URL which points to a CGI script at the Installation Server and contains the pin code. For example,
https://server.example.com/offline.cgi?pincode=a913a5bXTgd. - Enrollment Server redirects the web browser to that URL, or presents a clickable link.
- When the CGI script at the Installation Server is called, it checks if there is an EUF matching the pincode. If yes, the script checks the age of the EUF. If the file is older than a predefined time limit (e.g., 5 minutes), an error message is generated and processing stops.
- If the file age is OK, the script (See Appendix for further instructions for implementing this phase)
- Generates User Info package ("Via package" bootstrapping strategy is recommended).
- Produces a list of required packages from the dependencies of the EP.
- Creates a temporary repository which contains all the required packages and the User Info package.
- Creates an install file which contains
- The User Info package and
- The URL to the local repository on the device.
- Generates a zip file from the repository and the install file
- The script outputs the zip file with appropriate content type definitions. See Appendix.
- User connects the device to the desktop computer via USB cable.
- User copies the zip file to her device.
- At the device, the user extracts the repository and the install file from the zip file.
- User taps the install file to invoke the Application Manager, which installs the User Info package and all the packages in the dependency chain.
[edit] Components
- Web application (CGI script) running at Enrollment server
- Web application (CGI script) running at Installation server
[edit] Firewall rules
Same as in previous two strategies, depending on which server topology is used
[edit] Security considerations
- None
[edit] Pros and cons
- + Enables provisioning at remote locations
- + Fairly simple to use
- - Can be fairly laborious to implement
- - Presumably slow and storage space consuming
[edit] Summary
Here we looked at the tried out solutions for provisioning but some readers might be interested to read our alternative solution considerations or about future prospects for provisioning. If on the other hand these solutions suited already your needs you can move onward to provisioning summary.
- This page was last modified on 21 January 2011, at 11:18.
- This page has been accessed 11,761 times.