Enterprise Deployment Guide
This document is an unofficial guide as the Nokia N900 is not categorized as an enterprise device.
Contents |
[edit] Table of contents
- N900 Enterprise Deployment Guide
[edit] N900 and Maemo
The Nokia N900 is a powerful mobile computer with a phone feature. One area where the capabilities of N900 can be harnessed is the Enterprise environment. The device can be configured easily for providing access to corporate services and resources like:
- intranet web pages
- instant messenger
- VoIP services
The open architecture of the Maemo platform enables the integration of such enterprise services with minimal effort.
[edit] Purpose
This document describes the steps involved in deploying Nokia N900 in Enterprise environment. The primary objective of deploying the device in Enterprise environment is to improve the productivity of users in their work life.
[edit] Scope of document
The document gives examples of software that can be installed and configured on the N900 for the Enterprise environment. Additionally the document describes the infrastructure to be put in place for installing the device side software.
[edit] Enterprise environment
Enterprise environments vary greatly and it is impossible to give a description that fits any company. However, most companies utilize a rather similar strategy in controlling access to their networks and the following description is rather close to most common solutions.
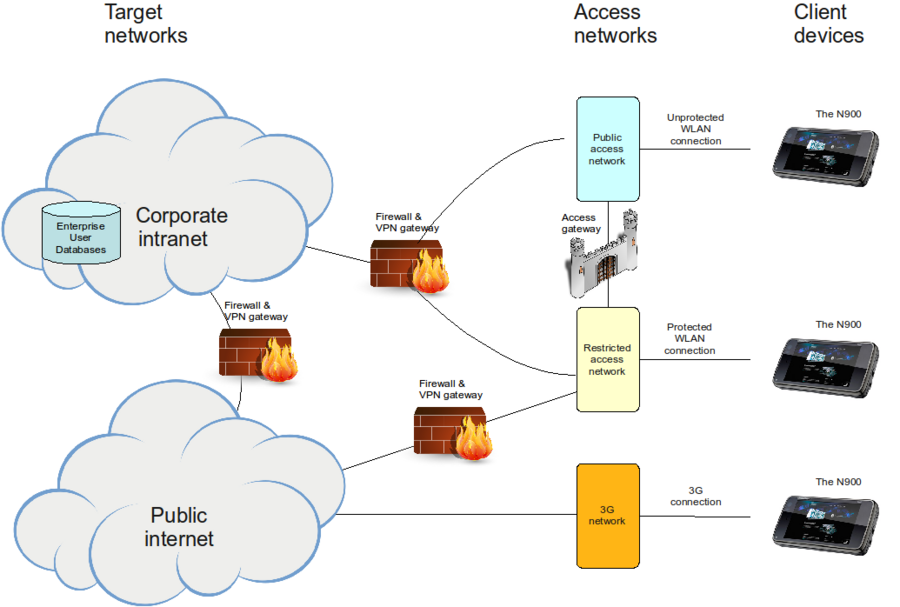
Figure 1 describes a typical arrangement of networking components at an enterprise. The picture is simplified and only components that are relevant for Enterprise provisioning are displayed.
Typically, corporate intranet is not directly accessible via WLAN connection due to obvious security implications. Instead, WLAN connections allow access to some "lobby" network. These lobby networks might or might not allow access to the public Internet. Lobby networks might be public, or they might be protected using some WLAN encryption technology.
The arrangement shown in Figure 1 consists of two different kinds of lobby networks and an access gateway between these. In addition, there is usually a 3G access network. Arrangements in different enterprises may vary, but the picture shows typical ways a device can be connected. Relevant characteristics of these networks are
- Public access network:
- Access is public, features are limited
- No connection to public Internet
- Mostly used for VPN connections to corporate intranet
- Might offer access to public Internet via authenticating gateway
- Restricted access network
- Access is restricted, features are unlimited
- Connection to public Internet
- Uses some WLAN encryption technology
- Device is unable to use the network until encryption keys are delivered
- 3G network
- Unrestricted access to public Internet
- No simultaneous access to WLAN networks above
[edit] Provisioning
Provisioning strategies are ways to get the device configured for enterprise use so that the user doesn't have to manually install and configure all the software on the device.
The selection of the provisioning strategy has a strong influence in every subsequent step and it is best to start by reading the provisioning introduction which is a highly recommended reading for first time readers to understand our terminology better.
- This page was last modified on 25 January 2011, at 08:50.
- This page has been accessed 22,264 times.